An Essential Buyer’s Guide to AD Threat Detection & Response
Active Directory continues to be a primary target for cyberattackers—it’s involved in 9 out of 10 cyberattacks. Yet many organizations fail to prioritize AD threat detection and response, which puts the organization’s most critical assets at risk. AD is the core identity store for 90% of organizations worldwide. If AD is breached, an attacker gets virtually unrestrained access to the organization’s entire network and resources. Protecting AD requires solutions that help prevent, remediate, and recover from AD attacks.
Organizations struggle to identify the optimal solutions for protecting AD because of several challenges, including the false assumption that AD protection is covered by other solutions. In fact, protecting AD requires AD-specific security and recovery. Many organizations have legacy AD implementations with risky configurations that have accumulated over time. Addressing those vulnerabilities requires AD expertise that many organizations lack. Complex hybrid identity environments make it difficult for IT operations and security teams to detect and correlate malicious changes across on-prem AD and Azure AD that could signal an attack. And if a cyberattack on AD succeeds, recovering AD is a complicated, time-consuming manual process that can cost the organization days or weeks of downtime. A layered identity system defense is the best strategy for protecting the organization’s critical AD infrastructure.
How can your organization take an identity-first security approach to ensure that your AD threat detection and response solution will protect AD before, during, and after an attack?

- Why AD is critical to organizations—and yet AD security is overlooked
- Primary challenges in protecting AD
- Watchlist for hybrid AD defense capabilities that are essential to protecting AD
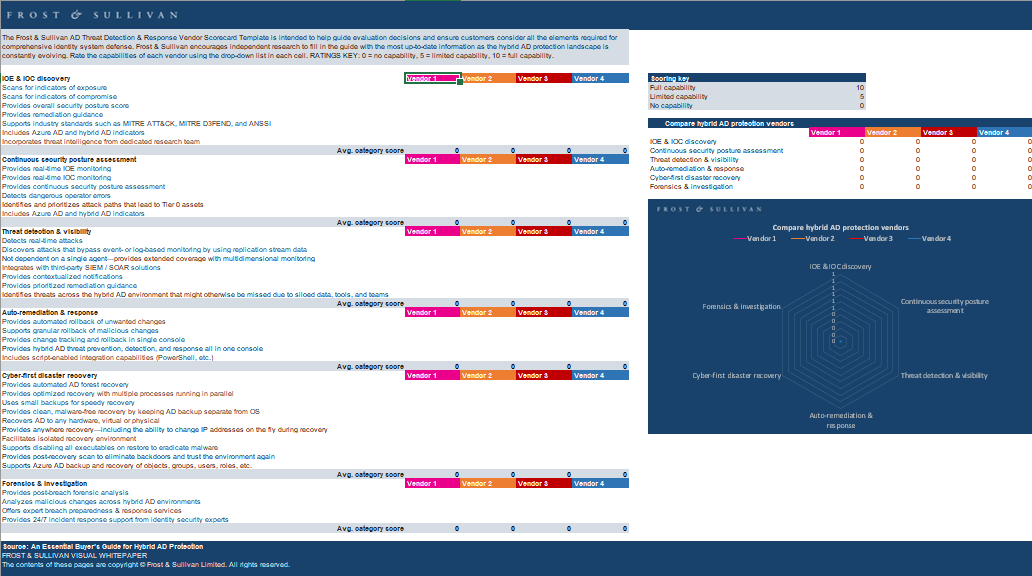
- Score solutions providers on AD threat detection and response capabilities in 6 categories
- See a visual comparison of relative strengths and weaknesses of vendors across categories
- Use the template as the basis of an RFP process to improve overall security posture by prioritizing solutions that protect AD before, during, and after an attack
Download the Complimentary Article
"*" indicates required fields